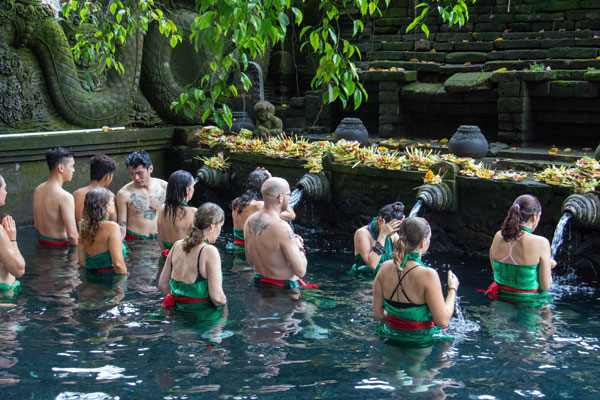Première fois à Bali ?
Se déplacer et passer du temps dans différentes parties de Bali est facile et gratifiant.
Peu de voyageurs restent dans un seul hôtel pour toute la durée de leurs vacances. Il est devenu très courant de voyager dans différents endroits et de voir ce que chaque zone a à offrir. Bali n’est pas très grande, il est donc facile de passer d’un endroit à un autre lorsque vous souhaitez changer d’hébergement.
Suggestions d’itinéraire pour les visiteurs de Bali pour la première fois (séjour entre 10 jours et 3 semaines)
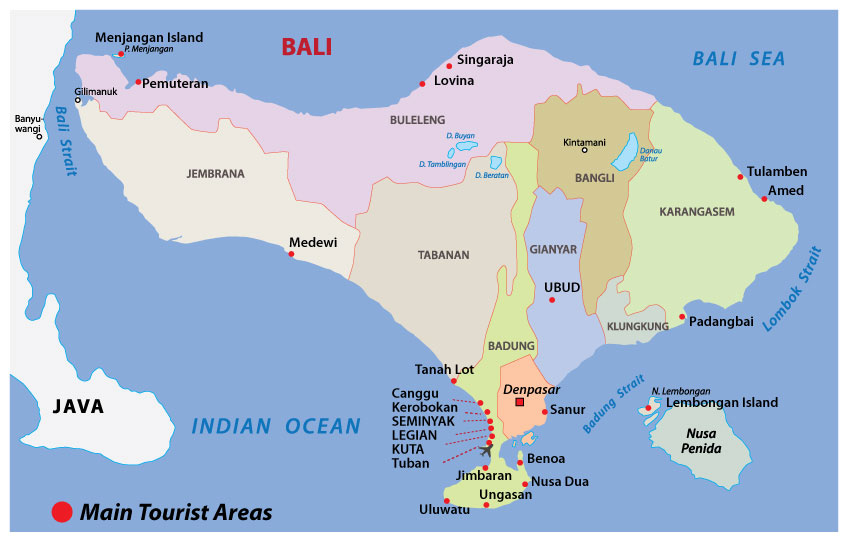
D’abord, prenez le temps d’explorer le Sud et d’arriver tôt pour vous habituer au fuseau horaire et au climat : Quelques jours à Sanur, Jimbaran ou Nusa Dua (arrivée facile et détente). (2-4 nuits)
Ensuite, faites du tourisme et explorez le centre. Déménagez à Ubud pour découvrir la culture et les sites naturels du centre et du nord de Bali (excursions et visites, détente, santé, yoga, nature). (3-5 nuits)
Si vous en avez le temps, allez sur les îles de Lembongan et Ceningan pour une vie tropicale et plus simple comme celle de Bali il y a 30 ans (et une plongée incroyable). Ou bien, vous pouvez vous rendre aux Gilis, ce qui prend un peu plus de temps. (2-4 nuits)
Terminez votre voyage dans le sud en sortant, en faisant la fête, en faisant du shopping ou en vous détendant simplement au coucher du soleil à Kuta, Legian, Seminyak ou dans le nouveau et excitant Canggu. (3-5 nuits)
Avec de tels choix, vous pouvez faire beaucoup en peu de temps (disons deux à trois semaines).
Lorsque vous retournerez à Bali, il y aura encore plus à découvrir et à explorer. Depuis des décennies, Bali est une destination de voyage populaire, et elle l’est restée en raison de l’abondance de merveilles et de sagesse de l’île.
CONSEIL CHAUD – Gagnez du temps
Lorsque vous vous déplacez vers un autre endroit, nous vous recommandons d’utiliser le jour du départ pour faire du tourisme et de louer une voiture avec chauffeur. (économisez 10% sur les visites et les locations de voitures avec notre BaliCard).
Votre chauffeur viendra vous chercher après le petit-déjeuner et vous emmènera en excursion d’une demi-journée ou d’une journée complète. Il garde vos bagages en sécurité dans la voiture pendant que vous visitez des temples et d’autres sites intéressants avant de vous conduire à votre prochaine destination.
C’est un excellent moyen d’éviter de perdre du temps à voyager entre vos hébergements et vos destinations choisis tout en économisant de l’argent.

 English
English Indonesia
Indonesia Deutsch
Deutsch हिन्दी
हिन्दी